WHAT THE HASH? Data Integrity and Authenticity in American Jurisprudence - United States Cybersecurity Magazine

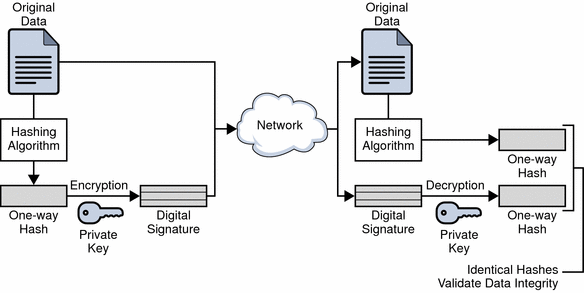
Hash Functions A hash function H accepts a variable-length block of data M as input and produces a fixed-size hash value h = H(M) Principal object is. - ppt download

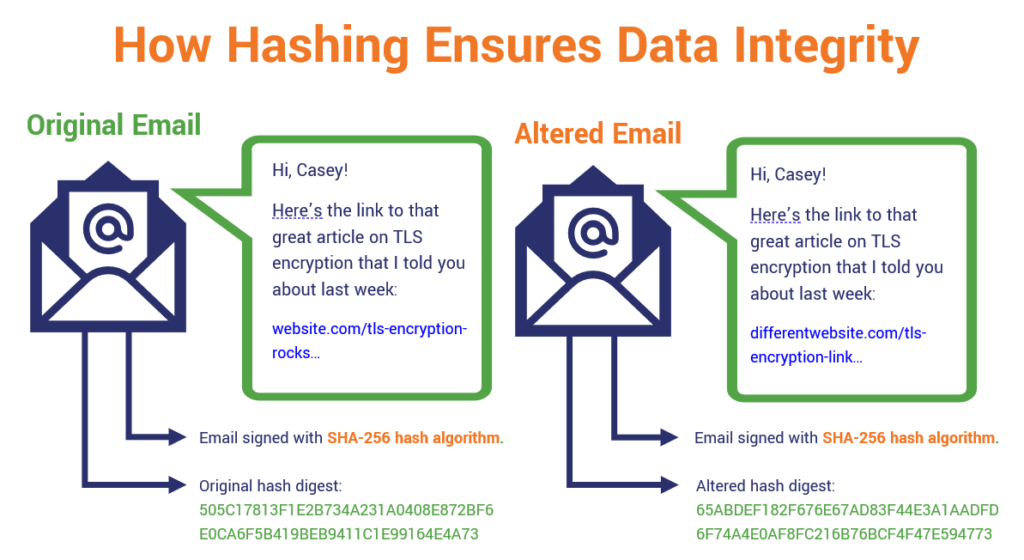
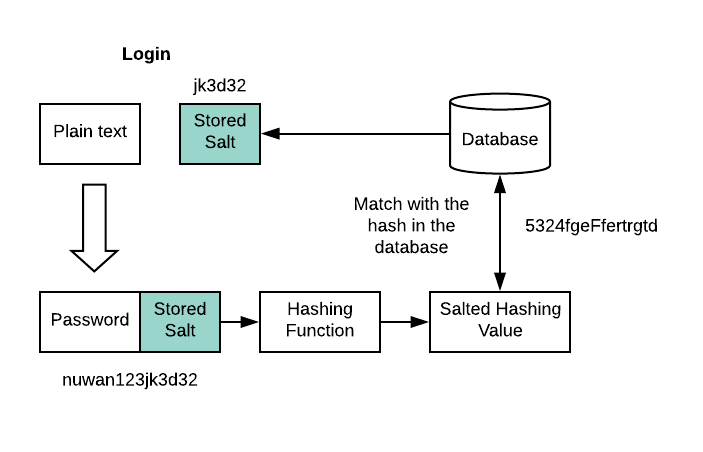

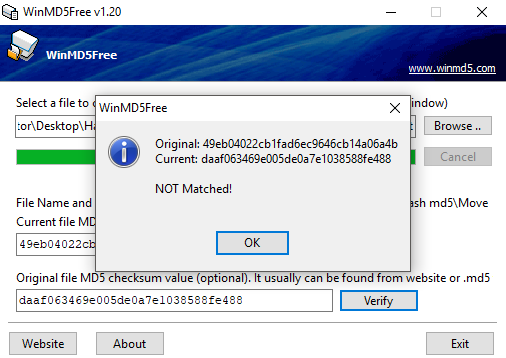
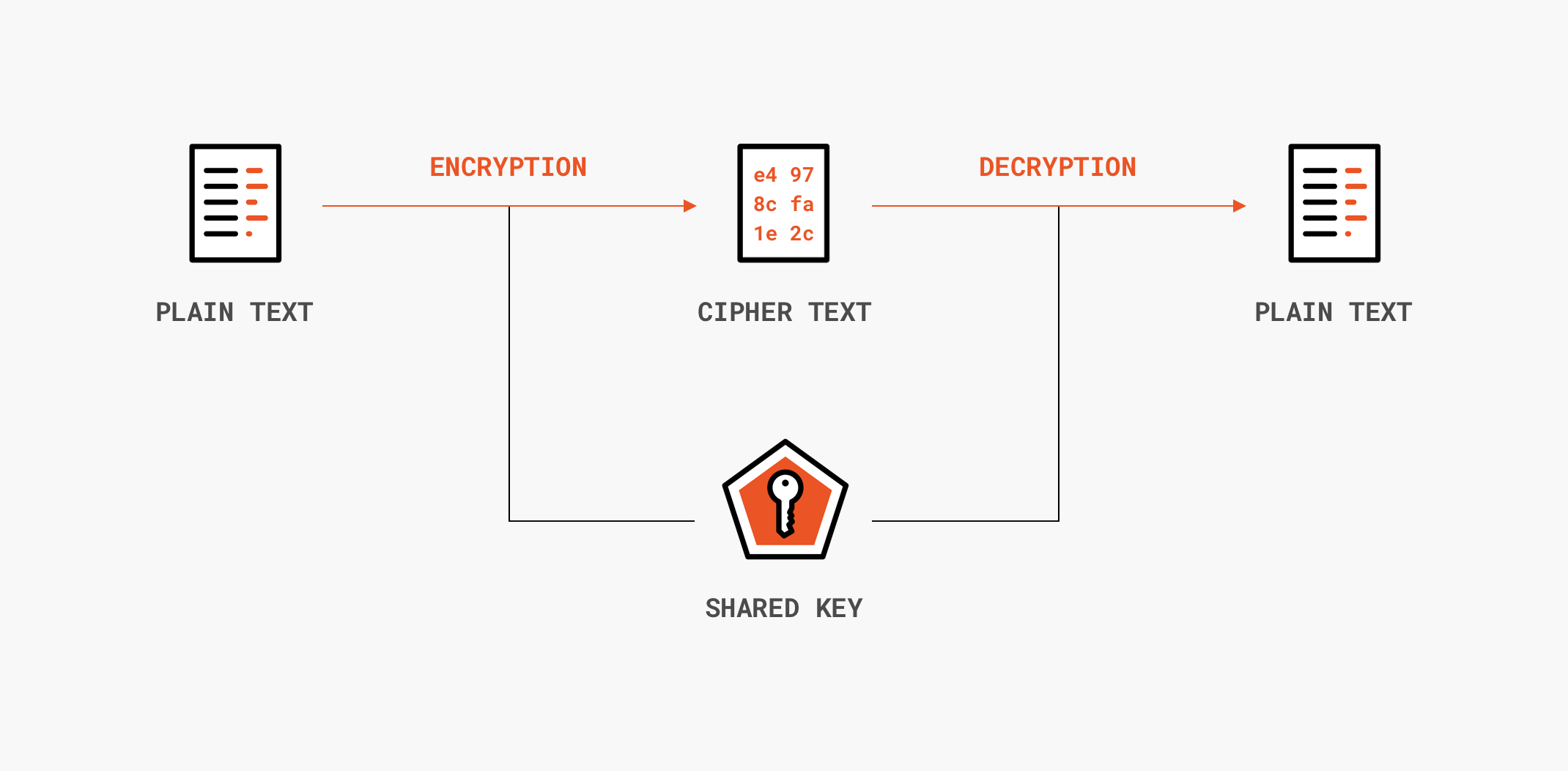
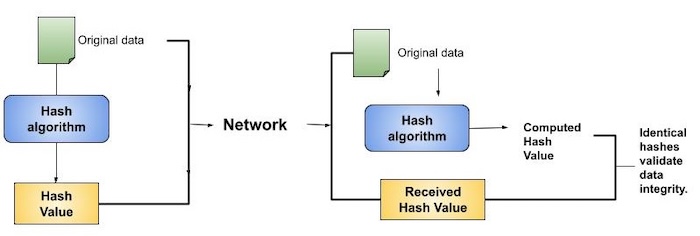


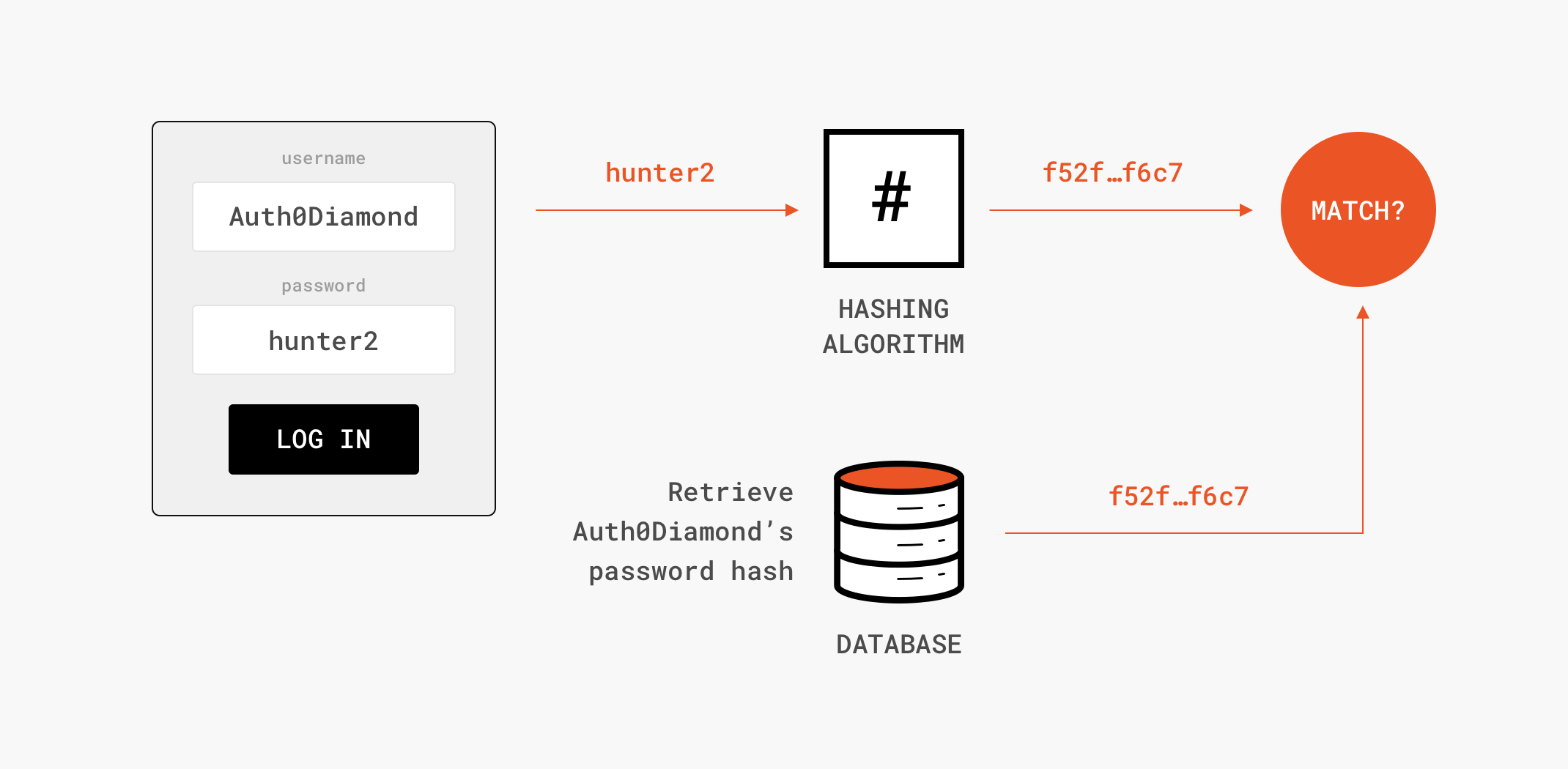


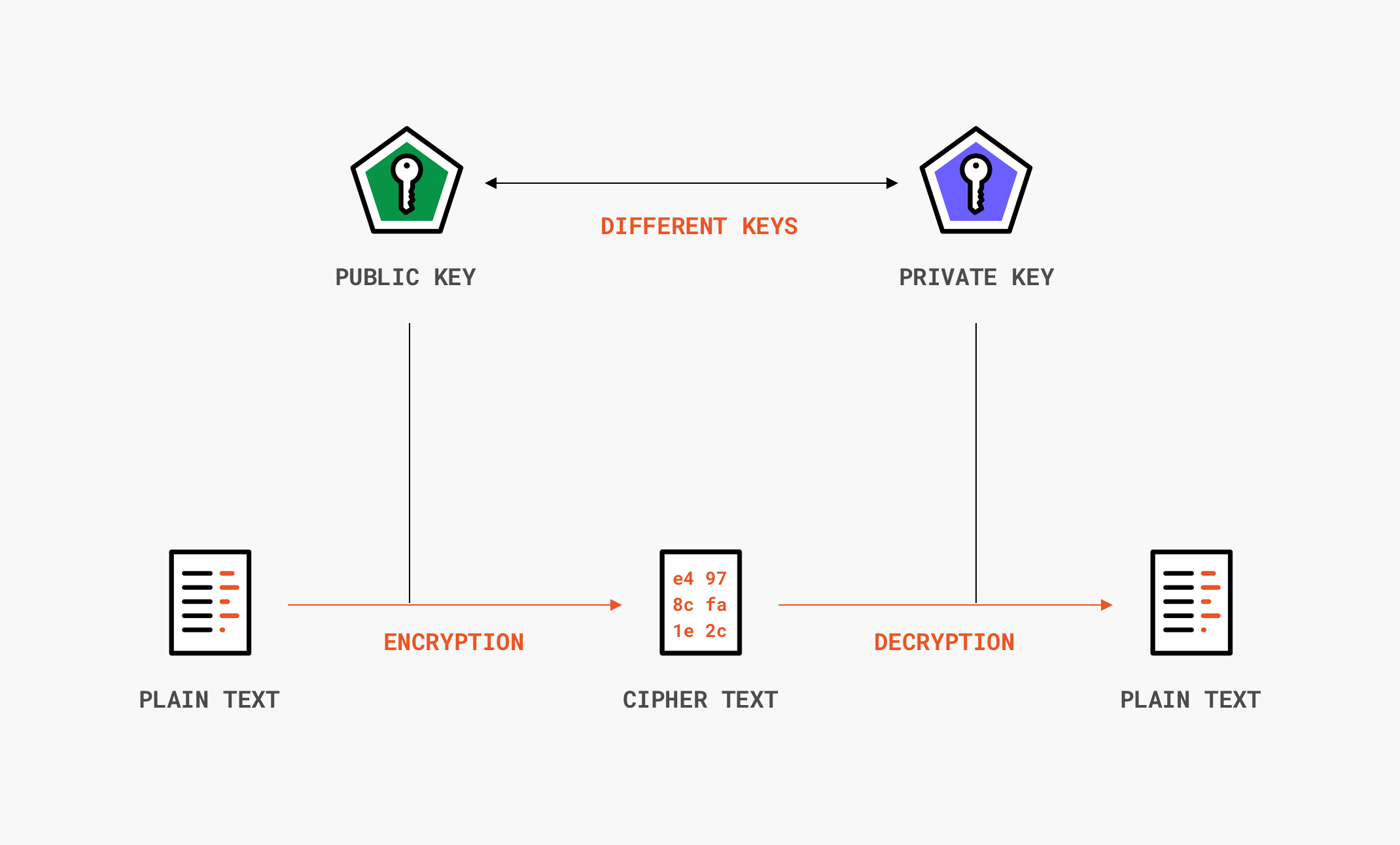
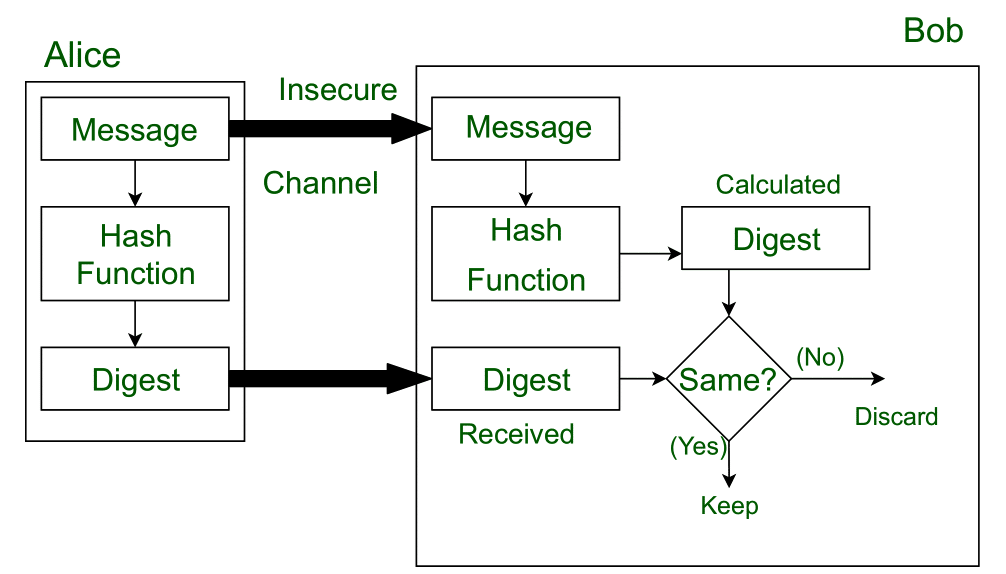
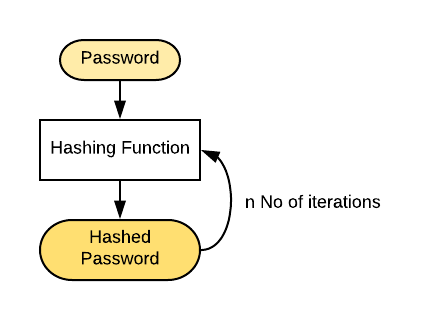
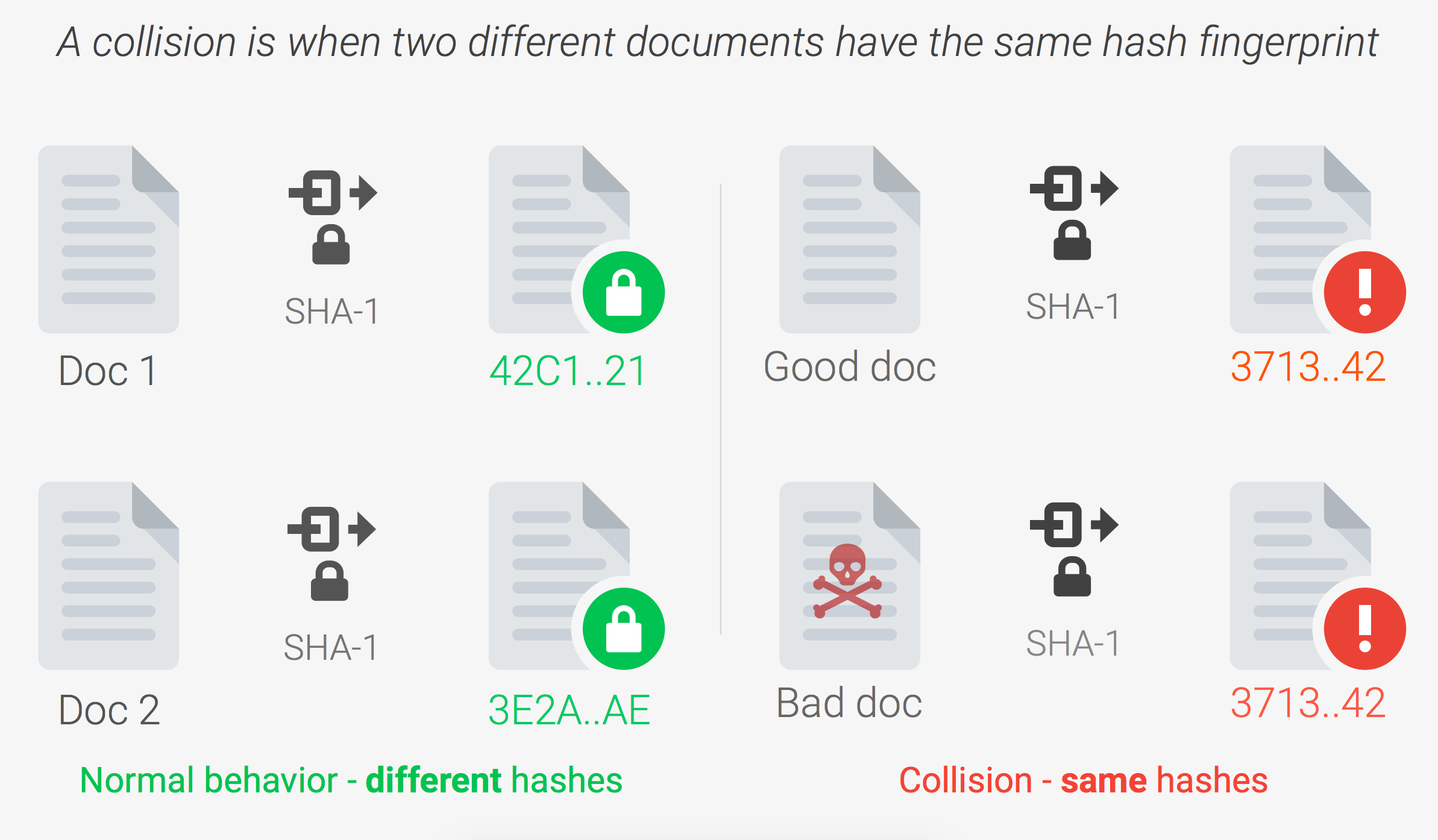

![What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard](https://positiwise.com/wp-content/uploads/2022/06/hash-function.png)